When it comes to security there is no finish line
Keeping our clients safe requires vigilance, conversation and consistency. Our method of keeping our clients safe, ensures the right levels of security today while also designed to anticipate your changing needs.
Innovation Safeguarded by Security
"For the past 10 years CKT has kept us the forefront of innovation without taking unnecessary risks and our security is always a top priority."
- C.M., CKT client since 2009

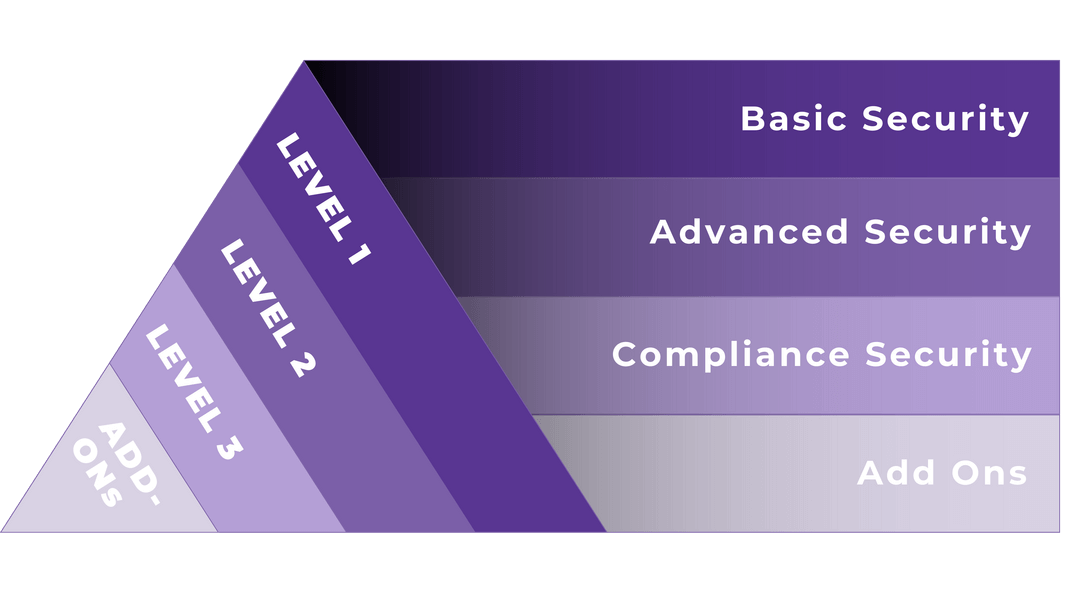
Basic Security
Our level one standard security offers fundamental protection to safeguard your digital assets.
- Next Generation Security — Protect servers and workstations with the latest endpoint security technology. Provides ransomware remediation and detailed forensic reports.
- Backups— Data currently backed up to local storage, cloud storage, or both. Backups are monitored daily and tested regularly.
- Multi-Factor Authentication— Configure MFA for Microsoft, Google, and as many lines of business applications as possible.
- Firewall and Remote Access— Maintain all firmware and updates. Configure SSL VPN and MFA access.
- Patching—Maintain updates on all servers and workstations. This includes operating system, mainstream software(i.e. Microsoft Office), and many line of business applications.
- Best Practices— Turn off IMAP/POP, set up SPF, DKIM, DMARC for email, close all unnecessary ports, increase password requirement complexity, delete unused accounts, geofencing, etc.
- Email Security— 3rd party email filter service to prevent malicious emails from getting through to end users. Includes phishing simulations.
- Cyber Security Awareness Training— Can you spot a phishing or spoofing email? Is it safe to click on the link? Educate your employees with both in-person and online training options. Upon request.
- Hard Drive Encryption— Configure encryption on all supported devices.
- Dark Web Monitoring— Be notified when employees’ credentials are exposed on the Dark Web. Know when to change your passwords to protect your assets. Cyber Liability Insurance
- Policy Review— Be confident you’re covered in case of a cyber-attack. Have an expert review your policy today.

Advanced Security
Level two specializes in insurance, providing the necessary safeguards to ensure you're fully covered and compliant with industry standards.
- Advanced Email Security— Includes Teams protection, scans for malicious links and files.
- Account Takeover Protection Password Management— Protect your passwords for both personal and business accounts. Manage access to company data and be able to add/remove users from a single point.
- Standard SEIM— Security event information manager, real time analysis of logs from workstations, servers, and cloud services like Microsoft Office 365.
- Zero Trust— Lock down your systems (remove local admin rights), set applications to only allow approved actions.

Compliance Security
Level three advanced security provides state-of-the-art measures to secure your data and infrastructure from even the most sophisticated attacks.
- Compliance SEIM— Security event information manager, real time analysis of logs from workstations, servers and cloud services like Microsoft Office 365.
- Data Classification— Guidance for conducting an inventory of data and classify which data needs to be secured.
- Internal Policy Review— Assist in designing, reviewing, deploying internal policies such as Acceptable Use, Incident Response and Data Destruction plans.
- Data Loss Protection (DLP)— Turn on basic rules to protect against transfer of personally identifiable information (PII) in Office 365 or Google Workplace.
- Threat Locker— Network access controls, group policy controls Security Risk Assessments and
- Vulnerability Scans— Assess how your technology environment compares to cyber security frameworks or compliance standards and best practices (ISO, NIST, HIPAA, PCI).
Add-Ons
Explore our range of additional enhancements to fine-tune your security solution, allowing you to customize and address specific security needs with precision.
- Mobile Device Management— Monitor and manage what’s happening on mobile devices.
- Single Sign-On— Sign in to multiple applications with a single ID that is automatic, authenticated and secure.
- Cyber QP— Privileged access management (know and verify who has access to your network and data), self-service password reset, etc.
“Our company has worked with CKT for several years and over time, we’ve appreciated CKT’s IT vision which has been tailored to our business and grounded in real world applications. The combination of tech, processes, and training is key to not experiencing any security breaches and we feel confident about the future. The team at CKT is very attentive to our needs and responds quickly to requests. No company is perfect, but when CKT realizes a product/service is not the right fit for us, they fight on our behalf which speaks volumes for how they have our best interests in mind.”
- N.F., CKT client since 2017



